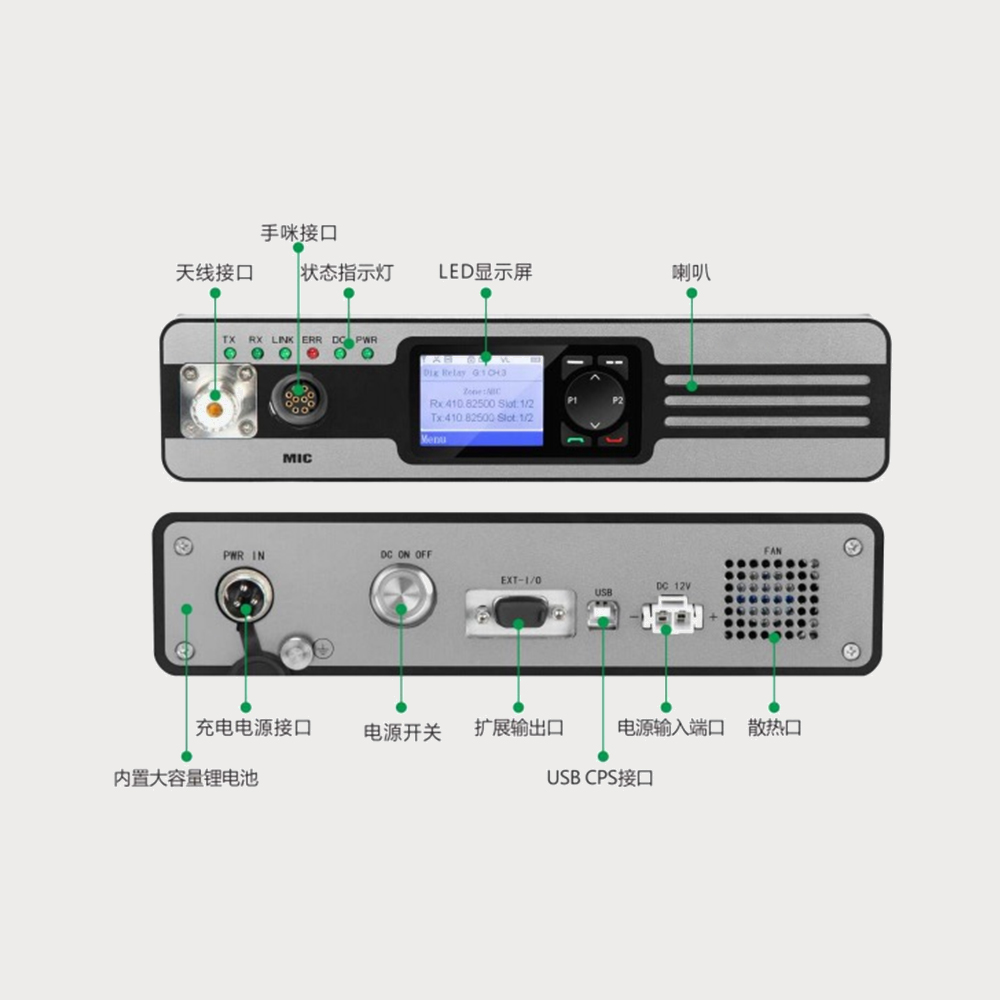
-
Wireless Remote Control Equipped with a wireless sensor remote control, it can remotely turn the device on and off, adjust the frequency of the shielder, with a sensing range of 1-10 meters.
- This product supports cross-network interconnectivity and all value-added services in GSM and WCDMA networks. This product is a brand new end-to-end voice encryption and decryption equipment suitable for the mainstream technology of 4G network and compatible with 3G and 2G network technologies. It has the ability of anti-AMR compression coding and anti-RPE-LTP compression coding. It has high speech intelligibility and good voice quality, and there is no problem of network compatibility.
- $ 5010
- 0 in Stock NowJR-MD68
-
GROUP
JR68
-
QUANTITY
- Contact Online
• Source Encryption Technology: Utilizes source encryption to secure user voice signals during transmission, ensuring end-to-end encrypted communication for mobile calls.
• Cross-Platform Encryption: Enables efficient encryption of call content between parties on different platforms, enhancing the security and compatibility of communications.
• End-to-End Security: Guarantees that all audio signals during the communication process are protected, maintaining confidentiality from the moment the call is initiated until it ends.
• Resilience Against Attacks: Even if an attacker gains access to the device, they cannot obtain the voice information due to the robust encryption, preventing unauthorized access to sensitive data.
• Isolation from Smart Devices: The encrypted communication cannot be linked or intercepted by any smart communication devices, ensuring privacy and preventing eavesdropping.
• No Additional Hardware/Software Required: The implementation of source encryption does not necessitate extra hardware or software support, making it a convenient and practical solution for securing communications.
Call security: Using information source encryption technology, the user's voice is directly encrypted into digital signals for transmission, to achieve end-to-end encryption of mobile phone calls, and to prevent leaks from the source;
Block recording: the phone recording function can be blocked at the same time during the call;
Standard Bluetooth protocol, suitable for most mobile phones; Charging port adopts USB universal TYPE-C interface;
End-to-end encryption, as a mobile phone companion, fully support all brands of mobile phones for encrypted calls;
AES-128 encoding dynamic encryption, one word one secret;
Metal body, physical button, long standby;
Adapt to mobile, telecom, Unicom three network communication;
Applicability principle: Suitable for high-end business people, government agencies, security units encrypted call needs;
Principles of ease of use: automatically connect to the phone when it is turned on, one-key encryption;
Product encryption system description: Shenzhou Minda Mi 1 adopts end-to-end source encryption technology, which has three parts.
1. The source voice is obtained from the mobile phone through Bluetooth, the voice is encoded in the mobile phone encryption device, and the encrypted signal is transmitted back to the mobile phone through Bluetooth;
2. Transmit the encrypted signal to the peer mobile phone through the mobile phone's mobile network or other channels;
3. The mobile phone receives the encrypted data sent by the peer end, and sends the data to the encryptor for decryption through the Bluetooth of the mobile phone, and the encryptor sends the decrypted sound back to the mobile phone for playback through the Bluetooth. Thus realize the process of encrypted speech;

 0
0